The plugin will be correctly reported in the reporter window. It's shows that even w/o debugging symbols we might find what the source of problem is, specially for third party plugins

All about my works and if u r a bit interested in Open Source, I recommend this blog!!!!

Here's a simple program that crashes relentlessly :P
include
#include
#include
#include
#include
#include
#include "client/linux/handler/exception_handler.h"
#include "client/linux/handler/linux_thread.h"
using namespace google_breakpad;
static ExceptionHandler* handler_process=NULL;
// Callback when minidump written.
static bool MinidumpCallback(const char *dump_path,
const char *minidump_id,
void *context,
bool succeeded) {
printf("%s is dumped\n", minidump_id);
return true;
}
static void *thread_crash(void *) {
ExceptionHandler handler_process(".", NULL, MinidumpCallback,
NULL, true);
while(true) sleep(1);
}
static void CreateCrashThread() {
pthread_t h;
pthread_create(&h, NULL, thread_crash, NULL);
pthread_detach(h);
}
int main(int argc, char *argv[]) {
int handler_index = 0;
CreateCrashThread();
int *a=NULL;
*a=0; //crash
while (true)
sleep(10);
return 0;
}
sanket@sanket-desktop:~/.subversion/google-breakpad-read-only/src/client/linux/handler$ gcc -c -gstabs -I ../../../ myCrash.cc
sanket@sanket-desktop:~/.subversion/google-breakpad-read-only/src/client/linux/handler$ g++ -gstabs -lpthread myCrash.o exception_handler.o linux_thread.o minidump_generator.o ../../minidump_file_writer.o ../../../common/convert_UTF.o ../../../common/string_conversion.o ../../../common/linux/file_id.o ../../../common/linux/guid_creator.o md5.o -o output
sanket@sanket-desktop:~/.subversion/google-breakpad-read-only/src/client/linux/handler$ ./output
5012fabe-5cd6-0ede-35eb05fb-77e2564c is dumped
sanket@sanket-desktop:~/.subversion/google-breakpad-read-only/src/client/linux/handler$ ls -lh 5012fabe-5cd6-0ede-35eb05fb-77e2564c.dmp
-rw------- 1 sanket sanket 18K 2009-03-30 16:55 5012fabe-5cd6-0ede-35eb05fb-77e2564c.dmp
The important thing is the generation of meaningful data from this dump. As I have used the normal libs( libstdc++ etc ) which dont have symbol information the output might not be that well percieved;
sanket@sanket-desktop:~/.subversion/google-breakpad-read-only/src/tools/linux/dump_syms$ ./dump_syms ../../../client/linux/handler/myCrash.o > myCrashSyms.sym
There's a python code which i searched and it's pretty good when creating Symbols from files in a very systematic File Hierarchy i shall use that code as a Part of a larger project that might need more tweaking... here's the link..
Continuing i shall show you the result after running minidump_stackwalk on the minidump file along with the symbols file we just created:
Here's the o/p when run with minidump_stackwalk bin.
------------------------------------------------------------------------------------------------------------------------
Operating system: Linux
0.0.0 Linux 2.6.27-11-generic #1 SMP Thu Jan 29 19:24:39 UTC 2009 i686 GNU/Linux
CPU: x86
GenuineIntel family 6 model 6 stepping 5
2 CPUs
Crash reason: SIGSEGV
Crash address: 0x80497d1
Thread 0 (crashed)
0 output + 0x17d1
eip = 0x080497d1 esp = 0xbfe87360 ebp = 0xbfe87378 ebx = 0xb7e14ff4
esi = 0x08053650 edi = 0x080496c0 eax = 0x00000000 ecx = 0x00005045
edx = 0xb7cb9b90 efl = 0x00010246
1 libc-2.8.90.so + 0x16684
eip = 0xb7cd1685 esp = 0xbfe87380 ebp = 0xbfe873e8
Thread 1
0 0xb7f87430
eip = 0xb7f87430 esp = 0xb7cb6d50 ebp = 0xb7cb6f28 ebx = 0xb7cb6f14
esi = 0xb7cb6f14 edi = 0xb7cb6f14 eax = 0xfffffdfc ecx = 0xb7cb6f14
edx = 0xb7e14ff4 efl = 0x00000246
1 output + 0x1929
eip = 0x0804992a esp = 0xb7cb6f30 ebp = 0xb7cb93b8
2 libpthread-2.8.90.so + 0x650e
eip = 0xb7f4350f esp = 0xb7cb93c0 ebp = 0xb7cb94b8
Loaded modules:
0x08048000 - 0x08056fff output ??? (main)
0x08057000 - 0x08057fff output ???
0x08058000 - 0x08058fff output ???
0xb7cbb000 - 0xb7e12fff libc-2.8.90.so ???
0xb7e13000 - 0xb7e14fff libc-2.8.90.so ???
0xb7e15000 - 0xb7e15fff libc-2.8.90.so ???
0xb7e19000 - 0xb7e25fff libgcc_s.so.1 ???
0xb7e26000 - 0xb7e26fff libgcc_s.so.1 ???
0xb7e27000 - 0xb7e27fff libgcc_s.so.1 ???
0xb7e28000 - 0xb7e4bfff libm-2.8.90.so ???
0xb7e4c000 - 0xb7e4cfff libm-2.8.90.so ???
0xb7e4d000 - 0xb7e4dfff libm-2.8.90.so ???
0xb7e4f000 - 0xb7f31fff libstdc++.so.6.0.10 ???
0xb7f32000 - 0xb7f35fff libstdc++.so.6.0.10 ???
0xb7f36000 - 0xb7f36fff libstdc++.so.6.0.10 ???
0xb7f3d000 - 0xb7f51fff libpthread-2.8.90.so ???
0xb7f52000 - 0xb7f52fff libpthread-2.8.90.so ???
0xb7f53000 - 0xb7f53fff libpthread-2.8.90.so ???
0xb7f6d000 - 0xb7f86fff ld-2.8.90.so ???
0xb7f88000 - 0xb7f88fff ld-2.8.90.so ???
0xb7f89000 - 0xb7f89fff ld-2.8.90.so ???
------------------------------------------------------------------------------------------------------------------------
It sums it all.... we can now start creating symbol compiled library and compile them with -gstabs etc to produce the appropriate symbols etc.
Chao :-)
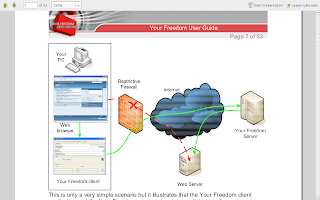
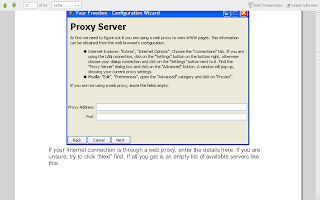 Now as far as i know this is the most critical step.... in Kgp here we use proxies and hence the fields are filled with those. But as far as i have gained knowledge many LAN's dont have proxy services... i am pretty amazed how they get them to work.... but if you have one put it there... else leave it blank.
Now as far as i know this is the most critical step.... in Kgp here we use proxies and hence the fields are filled with those. But as far as i have gained knowledge many LAN's dont have proxy services... i am pretty amazed how they get them to work.... but if you have one put it there... else leave it blank.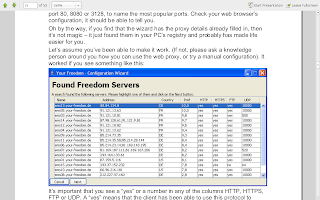
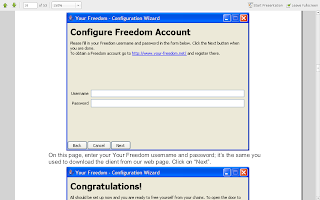
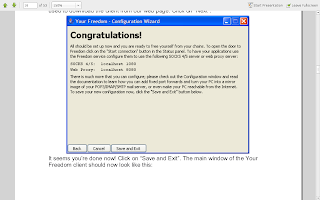
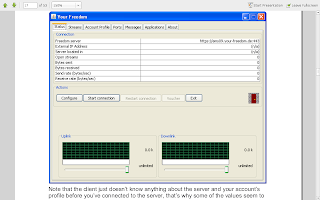
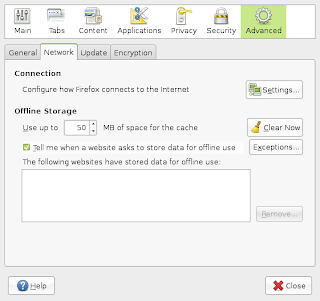
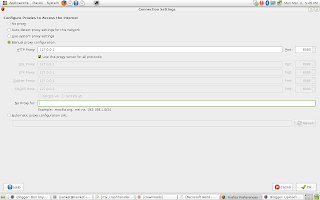 it's just full screened so dont be banboozled.... now put the placeholders as they are :)
it's just full screened so dont be banboozled.... now put the placeholders as they are :)